How to protect and discover secrets with Gitleaks?
Overview
Detecting and discovering secrets or (hardcoded) passwords in a code repository should be an ongoing process for everyone involved in code development. But this process should not take all the time so that we have more time to contribute to good code quality. Fortunately, nowadays there are various tools that help us to automatically check that no sensitive data is present. Secrets, such as API keys and passwords are a well-known example of this. Continue reading on how you can easily do this in your local dev environment with Gitleaks.
Installing
- Install gitleaks on your local system. I recommend using a package manager as the installation of packages will be easier and faster.
1# Mac OS
2brew install gitleaks
3
4# Windows
5choco install gitleaks
6
7# Linux
8curl -s https://api.github.com/repos/gitleaks/gitleaks/releases/latest | grep browser_download_url | cut -d '"' -f 4 | grep 'linux_x64' | wget -i -
9tar xf gitleaks_<replace with version>_linux_x64.tar.gz
10mv gitleaks /usr/local/bin
11rm gitleaks_<replace with version>_linux_x64.tar.gz
- Open the Git repo you want to detect secrets from, e.g.
cd <path-to-your-git-repository> - Perform an initial check to see if there are any leaks in your Git repository with
gitleaks detect . - Check the details with
gitleaks detect -v
Pre-Commit
Instead of manually execute gitleaks when you want to commit something to the Git repo we can automate this by using a pre-commit hook. As the name suggests this hook will execute whenever a git commit command is detected. Follow the steps below to activate this.
- Install pre-commit from https://pre-commit.com/#install
- Create a .pre-commit-config.yaml file at the root of your repository with the following content:
1repos:
2 - repo: https://github.com/pre-commit/pre-commit-hooks
3 rev: v4.4.0
4 hooks:
5 - id: check-yaml
6 - id: check-json
7
8 - repo: https://github.com/gitleaks/gitleaks
9 rev: v8.17.0
10 hooks:
11 - id: gitleaks
- Update the version of gitleaks in the file by executing
pre-commit autoupdate - Install the pre-commit hook with
pre-commit install
That's it! Every time you commit changes to your repository the pre-commit hook will scan the code with gitleaks and also validate yaml and json files. Read the next section on how to do that.
Usage
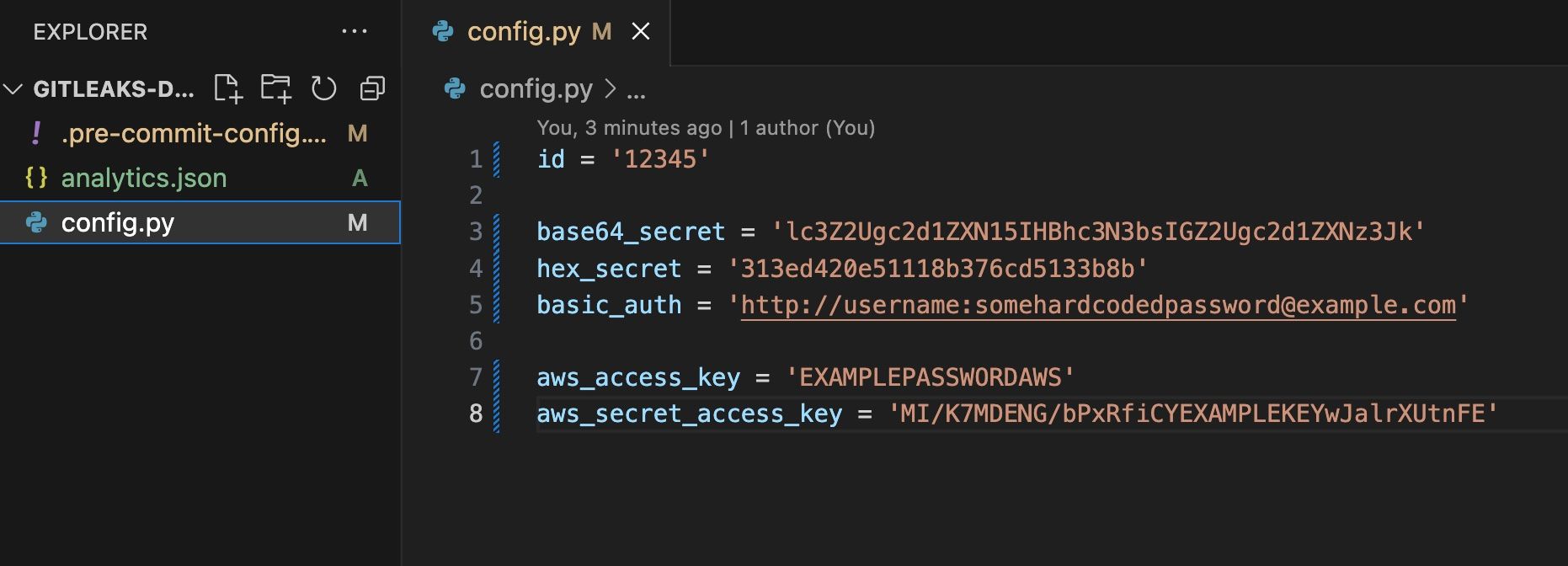
For testing purposes I will create a config.py file in the root of my Git repository. Now that gitleaks is active in my local dev environment, I expect that the pre-commit hook will detect hardcoded secrets.
1id = '12345'
2
3base64_secret = 'lc3Z2Ugc2d1ZXN15IHBhc3N3bsIGZ2Ugc2d1ZXNz3Jk'
4hex_secret = '313ed420e51118b376cd5133b8b'
5basic_auth = 'http://username:[email protected]'
6
7aws_access_key = 'EXAMPLEPASSWORDAWS'
8aws_secret_access_key = 'MI/K7MDENG/bPxRfiCYEXAMPLEKEYwJalrXUtnFE'
git add . # Stage all the changed files git commit -m "created config file" # Commit the staged files
When I try to commit the changes the pre-commit hook with gitleaks will prevent the commit because some leaks were found.
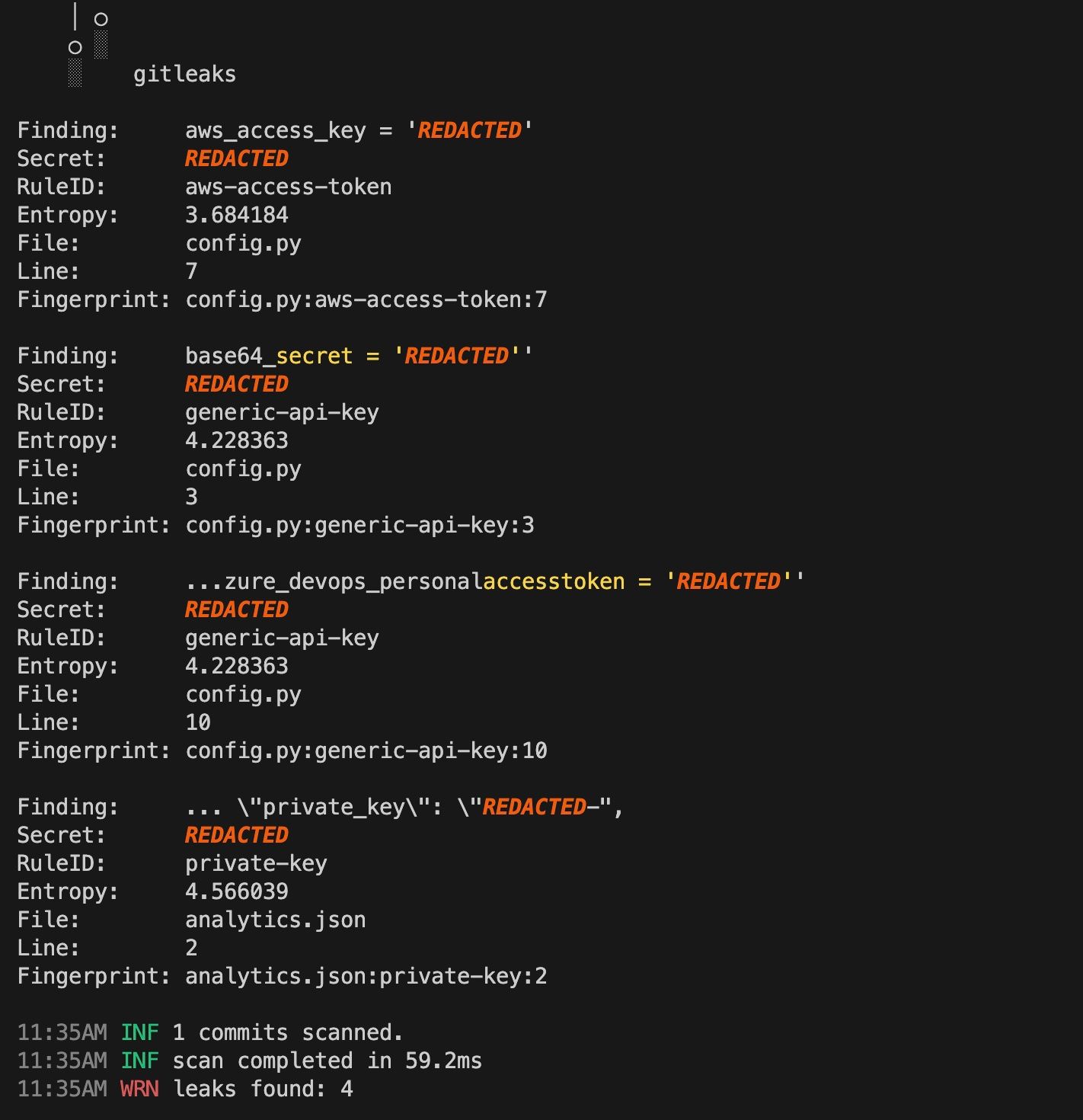
Note: Gitleaks ships with some default rules, but you can customize these rules to have more fine tuned rules in your project. To temporarily disable the gitleaks pre-commit hook you can prepend
SKIP=gitleaks: e.g.SKIP=gitleaks git commit -m "skip gitleaks check"to the commit command and it will skip running gitleaks.