How to secure passwords with gopass on multiple devices?
Overview
When we work with data we can use different ways of security. For my own project where I often use scripts on Linux machines, I figured out how to keep passwords safe. I used gopass. This is an open source UNIX password manager that uses gpg and version control with git. This means that passwords are encrypted and decrypted with gpg while keeping all the changes in a Git repository. This makes it very very flexible, because a git clone can always be made in case a new machine needs to be set up or if several devices want to use the password manager. If you are comfortable with the command-line interface keep reading, because we are going to execute multiple commands! I'm going to demonstrate these commands on a Linux (Debian OS) machine, but feel free to use another system.
Prerequisites
- One of the supported package managers
- (Optional) Git repository
- (Optional) Docker
Install and initialize gopass
When you never used gopass before the first step is to invoke the setup command. The setup process is very straightforward because of the step-by-step configuration. If you just want to play around with gopass I recommend to do this in an isolated environment like Docker. If you installed Docker already you can run the following command to start an empty nginx container which will be cleaned up again if you exit the shell:
1docker run --rm -it --entrypoint bash nginx
You can now run some commands to install gopass:
1apt update && apt upgrade && apt install sudo
1curl https://packages.gopass.pw/repos/gopass/gopass-archive-keyring.gpg | tee /usr/share/keyrings/gopass-archive-keyring.gpg >/dev/null
1cat << EOF | sudo tee /etc/apt/sources.list.d/gopass.sources
2Types: deb
3URIs: https://packages.gopass.pw/repos/gopass
4Suites: stable
5Architectures: all amd64 arm64 armhf
6Components: main
7Signed-By: /usr/share/keyrings/gopass-archive-keyring.gpg
8EOF
9sudo apt update
10sudo apt install gopass gopass-archive-keyring -y
Start the gopass configuration:
1gopass setup
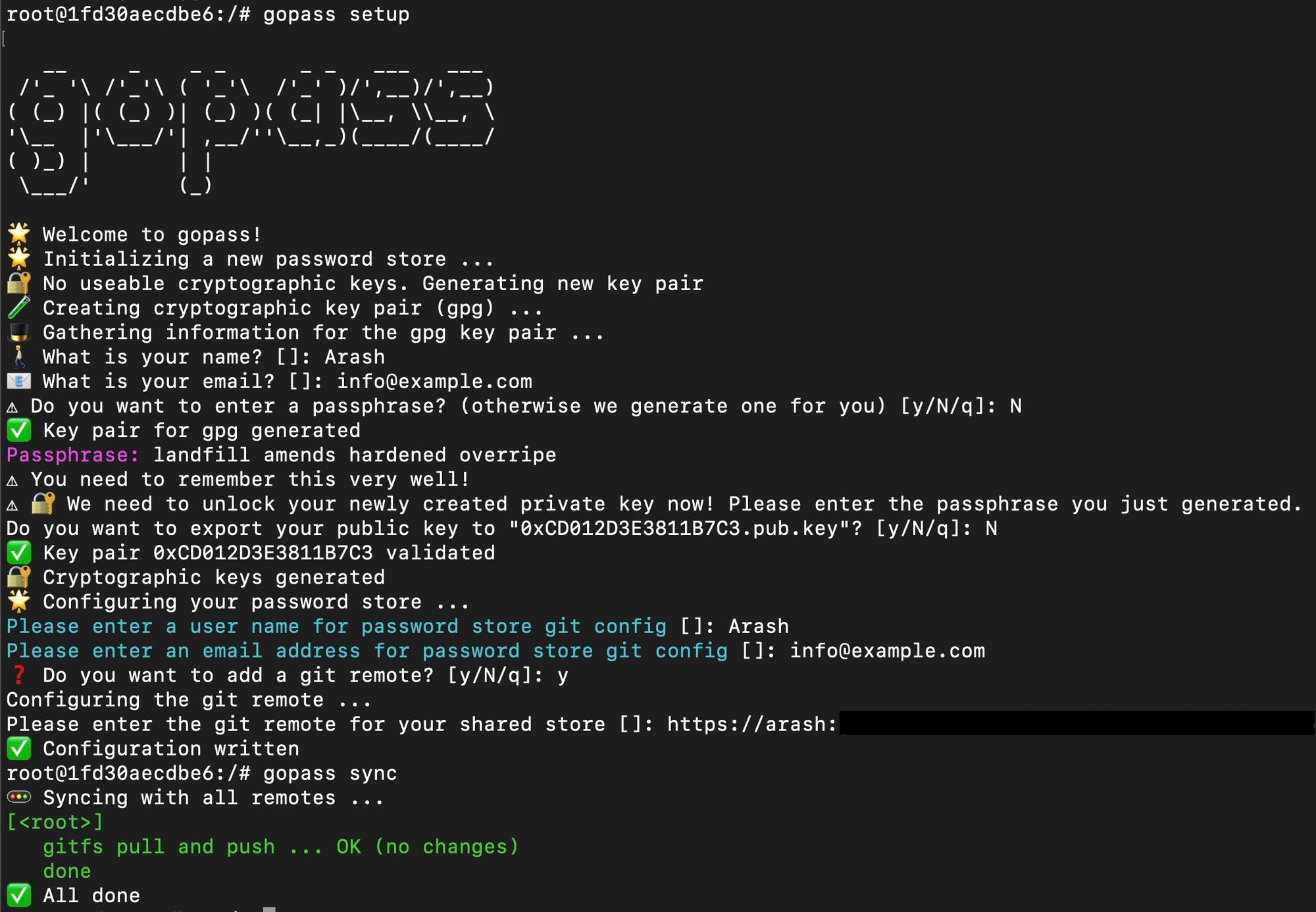
💡 You may use a password-protected SSH key to clone your Git repository instead of password-base usage of Git. Follow the instructions how to generate a new SSH key and add this to your Git repo on GitHub. Otherwise follow the instructions of your preferred Git provider.
Create passwords
When the setup is finished we can start creating new passwords with gopass. The command to create a password is easy. Gopass can check password for common flows, for example if the password is too short:
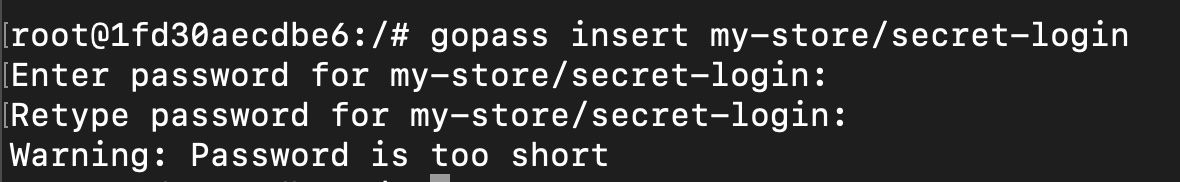
Note that gopass handles a logical structure for passwords. You can group them how you want it. It is up to you! Let's insert a more complex password in order to succeed the creation of the password:
1gopass insert my-store/secret-login
Gopass will prompt you to type in the password twice to confirm. Once confirmed the password will be encrypted with gpg. To be able to encrypt you need to type in your passphrase which you created or was created for you during the setup process.
When the new password is created we can list the new password with gopass ls. It will have the following structure:
gopass └── my-store/ └── secret-login
Gopass will automatically sync the new created password in your password store with Git which is now version controlled.
Setup gopass on second device
If you want to share your password store with another device gopass supports team sharing. This is a really nice feature since all passwords are now centrally maintained in Git. When gopass is installed on the second device it is not needed anymore to run gopass setup, but you can use gopass clone [email protected]:john/passwords.git.
In order to activate team sharing we need to make gopass aware that another device needs to be trusted. This works by adding a new recipient.
After the Git repository with the password store included is cloned on the second device the gpg public key needs to be exported. This can be done with gpg -a --export [email protected] > willy.pub.asc and then import on the first device with gpg --import < willy.pub.asc or you can just type gopass sync on the second device to also sync the public key to the Git repo of the password store. On the first device you can now fetch the Git changes with also typing gopass sync. It will prompt you to add the new public key of the second device. Confirm with y. The last thing we need to do on the first device is re-encrypting the existing passwords in the password store in order to give access to other recipients, in this case the second device:
1gopass fsck
2gopass sync
Now we need to add the new recipient with the e-mail address of the second device:
1gopass recipients add [email protected]
2gopass sync
(Optional) Remove passphrase of gpg key
You may want to remove the passphrase of the newly created gpg private key. For example when you want to use gopass in a script on a local device. First list the secret keys you want to edit:
1gpg --list-secret-keys
Note the e-mail address of the secret key and otherwise the public key id. Edit the key and change the password. First type in the existing passphrase and leave empty when you have to enter a new passphrase:
1gpg --edit-key [email protected]
2passwd
3quit